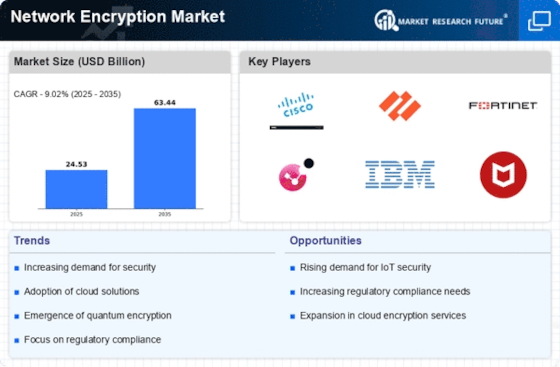
Regulatory Pressures
Regulatory pressures are increasingly shaping the landscape of the Network Encryption Market. Governments and regulatory bodies worldwide are instituting stringent data protection laws, compelling organizations to adopt encryption as a standard practice. For instance, regulations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) mandate that businesses implement adequate security measures to protect personal data. Failure to comply with these regulations can result in substantial fines and reputational damage. As a result, organizations are prioritizing encryption technologies to ensure compliance, thereby driving growth in the Network Encryption Market. This trend underscores the critical role of encryption in not only safeguarding data but also in meeting legal obligations.
Emergence of IoT Devices
The proliferation of Internet of Things (IoT) devices is a significant catalyst for the Network Encryption Market. As more devices become interconnected, the potential for data breaches increases, necessitating robust encryption solutions to secure communications. The IoT market is expected to witness exponential growth, with estimates suggesting that there will be over 75 billion connected devices by 2025. This surge in connectivity amplifies the need for encryption to protect sensitive information transmitted between devices. Consequently, the Network Encryption Market is likely to experience heightened demand as organizations seek to implement encryption protocols that can effectively secure their IoT ecosystems, thereby mitigating risks associated with data vulnerabilities.
Increasing Cyber Threats
The rise in cyber threats has become a pivotal driver for the Network Encryption Market. Organizations are increasingly recognizing the necessity of robust encryption solutions to safeguard sensitive data from unauthorized access and breaches. In recent years, the frequency of cyberattacks has escalated, with reports indicating that ransomware attacks alone have surged by over 150%. This alarming trend compels businesses to invest in advanced encryption technologies, thereby propelling the growth of the Network Encryption Market. As companies strive to protect their intellectual property and customer information, the demand for effective encryption solutions is likely to continue its upward trajectory, reflecting a broader commitment to cybersecurity.
Adoption of Cloud Services
The widespread adoption of cloud services is significantly influencing the Network Encryption Market. As organizations migrate their operations to the cloud, the need for secure data transmission becomes paramount. Encryption serves as a critical mechanism to protect data both at rest and in transit, ensuring compliance with various data protection regulations. Recent studies suggest that the cloud computing market is projected to reach a valuation of over 800 billion dollars by 2025, which inherently drives the demand for encryption solutions. Consequently, the Network Encryption Market is poised for growth as businesses seek to implement encryption protocols that align with their cloud strategies, thereby enhancing their overall security posture.
Growing Demand for Data Privacy
The growing demand for data privacy is a crucial driver of the Network Encryption Market. Consumers are becoming increasingly aware of their rights regarding personal data, leading to heightened expectations for privacy and security. This shift in consumer sentiment is prompting organizations to adopt encryption technologies as a means to protect sensitive information. Recent surveys indicate that over 80% of consumers express concerns about data privacy, which in turn influences their purchasing decisions. As businesses strive to build trust with their customers, the implementation of encryption solutions becomes essential. Thus, the Network Encryption Market is likely to expand as organizations prioritize data privacy initiatives, recognizing that encryption is a fundamental component of their overall data protection strategies.