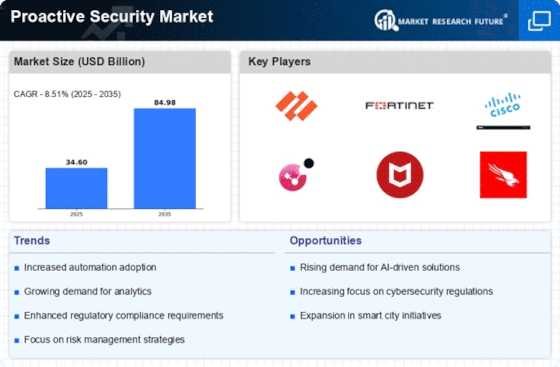
Top Industry Leaders in the Proactive Security Market

Proactive Security Market: Dive into the Latest News and Updates
In the ever-evolving cybersecurity landscape, simply reacting to threats is no longer enough. Organizations are shifting towards proactive security measures, seeking solutions that predict, prevent, and mitigate cyberattacks before they occur.
Some of Proactive Security Companies Listed Below:
- IBM Corporation (US)
- Corvil (Ireland)
- Altran (France)
- Cisco Systems Inc. (US)
- Palo Alto Networks, Inc. (US)
- Securonix, Inc. (US)
- LogRhythm, Inc. (Netherlands)
- Rapid7 (US)
- Symantec Corporation (US)
- FireEye, Inc. (US)
- McAfee, LLC (US)
- CyArx Technologies LTD (US)
- Oracle Corporation (US)
- AT&T (US)
- FUJITSU (Japan)
Strategies Fueling Growth:
-
Focus on Threat Intelligence and Predictive Analytics: Providing real-time threat feeds, vulnerability assessments, and AI-powered anomaly detection capabilities helps organizations anticipate cyberattacks and prioritize their defense efforts. -
Automation and Orchestration: Implementing automated security tools for incident response, patch management, and threat mitigation streamlines operations and reduces human error, enabling faster and more effective responses to emerging threats. -
Continuous Monitoring and Threat Hunting: Actively monitoring networks, endpoints, and user behavior for suspicious activity enables early detection of anomalous activities and proactive intervention before attackers can cause significant damage. -
Integration with Existing Security Ecosystems: Proactive security solutions that seamlessly integrate with existing security platforms, tools, and infrastructure optimize workflows and enhance the overall security posture of an organization.
Market Share Decoding: Key Factors to Consider:
-
Product Portfolio Breadth and Functionality: Companies offering diverse proactive security features, including threat intelligence, AI-powered analytics, automated response tools, and vulnerability management, cater to wider needs and attract larger customer bases. -
Industry Expertise and Compliance Focus: Providers with deep understanding of specific industries and their unique threat landscapes can tailor solutions for optimal proactive defense within those sectors, gaining an edge in niche markets. -
Cloud-Based Deployment and Scalability: Cloud-based proactive security platforms offer flexible deployment options, centralized management, and lower upfront costs, making them increasingly attractive to organizations of all sizes. -
Compliance and Regulatory Certifications: Demonstrating compliance with data privacy regulations and industry standards builds trust and ensures compatibility with existing legal frameworks, particularly relevant for organizations handling sensitive data.
New and Emerging Stars: Illuminating the Proactive Path:
-
AI-powered Deception Technologies: Startups like TrapX and CyberArk focus on deploying decoy systems and honeypots to attract and deceive attackers, gaining valuable insights into their tactics and mitigating real-world attacks. -
Behavioral Modeling and User Entity and Behavior Analytics (UEBA): Companies like Splunk and Exabeam utilize advanced behavioral analytics to detect anomalous user activity and identify insider threats before they cause harm. -
Cybersecurity Automation and Orchestration Platforms (SOAR): Startups like Demisto and Swimlane offer tools for automating incident response workflows, threat remediation processes, and security operations, streamlining response times and optimizing security resources.
Latest Company Updates:
-
Cybersecurity News, Insights and Analysis | SecurityWeek:- Researchers have warned about the potential misuse of powerful AI models for online disinformation, cyberattacks, or the creation of bioweapons.
- A San Francisco startup has received fresh capital to compete in the crowded identity and access management space.
- Noteworthy stories include fake Lockdown Mode, a new Linux RAT, jailbreaking AI, and an entire country's DNS hijacked.
- WordPress 6.4.2 has patched a flaw that could be exploited to execute arbitrary code.
- The Russian threat actor APT28 has been exploiting a no-interaction Outlook vulnerability in attacks against 14 countries.
- The US and UK have announced charges and sanctions against two hackers working with Russia's FSB security service.
-
The Hacker News | Trusted Cybersecurity News Site :- The Hacker News is a trusted and popular cybersecurity publication that provides breaking news, actionable insights, and analysis for information security professionals.