Growing Cyber Threat Landscape
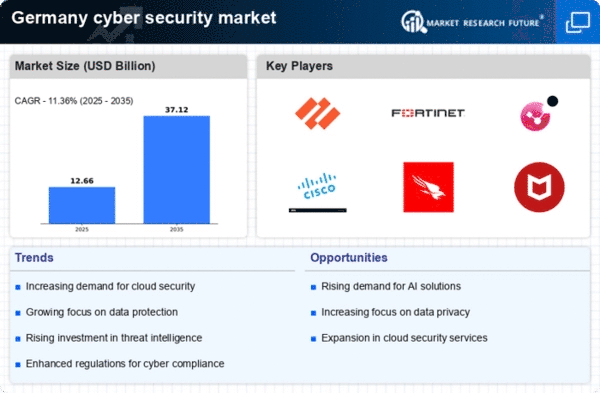
The cyber security market in Germany is experiencing a notable surge due to the increasing frequency and sophistication of cyber threats. Recent data indicates that cyber incidents have escalated by approximately 30% over the past year, prompting organizations to prioritize their security measures. This heightened threat landscape compels businesses to invest in advanced security solutions, thereby driving growth in the cyber security market. The rise in ransomware attacks and data breaches has led to a greater awareness of vulnerabilities, pushing companies to adopt comprehensive security frameworks. As a result, the demand for innovative technologies and services within the cyber security market is expected to continue its upward trajectory, reflecting the urgent need for robust defenses against evolving cyber risks.
Digital Transformation Initiatives
The ongoing digital transformation across various sectors in Germany is a key driver of the cyber security market. As organizations increasingly adopt cloud computing, IoT devices, and mobile technologies, the attack surface expands, necessitating enhanced security measures. A recent survey revealed that over 70% of German companies are investing in digital transformation initiatives, which inherently increases their vulnerability to cyber threats. Consequently, there is a growing recognition of the need for integrated security solutions that can protect digital assets. This trend is likely to fuel demand for advanced cyber security technologies, as businesses seek to secure their digital infrastructures and maintain operational continuity. The cyber security market is thus positioned to benefit from this shift towards digitalization, as organizations prioritize security in their transformation strategies.
Regulatory Pressures and Compliance
In Germany, the cyber security market is significantly influenced by stringent regulatory requirements aimed at protecting sensitive data and ensuring compliance. The implementation of the General Data Protection Regulation (GDPR) has heightened the focus on data privacy, compelling organizations to enhance their cyber security measures. Companies face substantial fines for non-compliance, which can reach up to €20 million or 4% of global turnover, thus incentivizing investments in security solutions. Furthermore, the Federal Office for Information Security (BSI) has established guidelines that necessitate adherence to specific security standards. This regulatory environment fosters a robust demand for cyber security services, as organizations strive to meet compliance requirements while safeguarding their assets, ultimately propelling the growth of the cyber security market.
Increased Awareness of Cyber Security Risks
The heightened awareness of cyber security risks among businesses and consumers in Germany is driving growth in the cyber security market. Recent studies indicate that approximately 60% of German enterprises consider cyber security a top priority, reflecting a shift in mindset towards proactive risk management. This awareness is largely attributed to high-profile data breaches and cyber incidents that have garnered media attention, leading to a more informed public. As organizations recognize the potential financial and reputational damage associated with cyber threats, they are more inclined to invest in comprehensive security solutions. This trend suggests that the cyber security market will continue to expand as stakeholders increasingly prioritize risk mitigation and resilience against cyber attacks.
Investment in Cyber Security Education and Training
The cyber security market in Germany is also being propelled by a growing emphasis on education and training in the field of cyber security. With the increasing complexity of cyber threats, there is a pressing need for skilled professionals who can effectively manage security challenges. Recent reports indicate that the demand for cyber security training programs has surged by over 40% in the past year, as organizations seek to equip their workforce with the necessary skills. This investment in education not only enhances the capabilities of existing employees but also attracts new talent to the industry. As a result, the cyber security market is likely to benefit from a more skilled workforce, which is essential for addressing the evolving landscape of cyber threats and ensuring robust security measures.