Top Industry Leaders in the Zero Trust Security Market

Competitive Landscape of Zero Trust Security Market:
The Zero Trust Security market is experiencing explosive growth, fueled by rising cyber threats and the increasing adoption of hybrid and cloud computing. This dynamic landscape is teeming with established players, emerging challengers, and diverse strategies, all vying for a piece of this lucrative pie. Understanding this competitive landscape is crucial for any organization seeking to navigate the complexities of Zero Trust adoption.
Key Players:
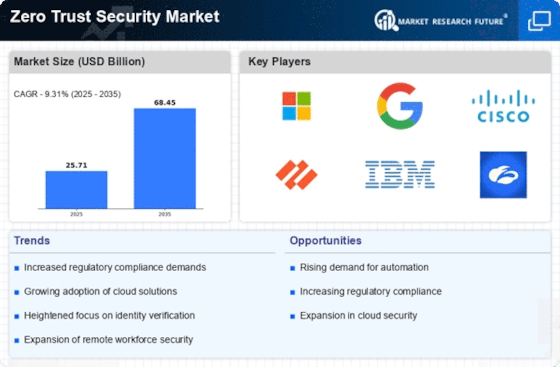
- Cisco Systems, Inc.
- IBM
- Akamai Technologies
- Google LLC
- Check Point Software Technologies Ltd.
- Pulse Secure, LLC.
- Palo Alto Networks.
- Zscaler, Inc.
- Deloitte Touche Tohmatsu Limited
- Accenture
- PWC
- Tata Consultancy Service Limited
- Microsoft Corporation
- Com
- KPMG
- Boston Consultancy Group
- Forcepoint and McKinsey & Company
Strategies Adopted:
- Product Innovation: Continuous development of next-generation Zero Trust solutions with advanced features like dynamic authorization, context-aware access control, and AI-powered threat detection is key. Players are also integrating with emerging technologies like blockchain and quantum security to stay ahead of the curve.
- Partnership Ecosystem: Building strong partnerships with cloud providers, systems integrators, and security consulting firms allows for comprehensive offerings, expanded customer reach, and accelerated market penetration. Collaborations with niche players foster innovation and address specific customer needs.
- Subscription-Based Models: Shifting from traditional perpetual licensing to subscription-based models with flexible pricing plans and consumption-based pricing helps attract cost-conscious customers and generate recurring revenue streams.
- Compliance and Regulation: Aligning solutions with evolving data privacy regulations like GDPR and CCPA builds trust and opens doors to new markets.
Factors for Market Share Analysis:
- Product Portfolio Breadth and Depth: A comprehensive Zero Trust solution encompassing identity and access management, network security, endpoint protection, and data security offerings provides a competitive edge.
- Cloud-Native Architecture and Integrations: Seamless integration with popular cloud platforms and offering cloud-delivered solutions are essential for addressing the modern enterprise landscape.
- Scalability and Flexibility: Ability to adapt to diverse customer needs and scale to accommodate future growth is crucial for long-term success.
- Customer Support and Professional Services: Robust customer support, training programs, and professional services for Zero Trust implementation and ongoing optimization foster trust and loyalty.
New and Emerging Companies:
Startups like Accolade, StackRox, and Styra are bringing fresh perspectives and disruptive technologies to the market. They focus on specific areas like container security, API security, and workload identity management, offering innovative solutions that address emerging needs in the Zero Trust landscape.
Current Company Investment Trends:
- Acquisitions and Mergers: Established players are actively acquiring smaller companies with specialized expertise, filling gaps in their offerings and expanding their reach into new market segments.
- Venture Capital Funding: The Zero Trust market attracts significant venture capital investment, fueling the growth of promising startups and fueling innovation in the space.
- Focus on R&D: Continuous investment in research and development is crucial for staying ahead of the curve and developing next-generation solutions that address evolving cyber threats and user needs.
Latest Company Updates:
Come 2023, .The ExtraHop Zero Trust Extension for Netskope was released today, according to ExtraHop, a pioneer in cloud-native network detection and response (NDR). With its comprehensive visibility into the behaviours and communications of devices and services in distant and distributed networks, across on-premises, hybrid, and cloud environments, at any size, ExtraHop's most recent integration will assist businesses on their zero trust path.
Zero Trust Maturity Model (ZTMM) version 2, released in 2023 by the US Cybersecurity and Infrastructure Security Agency (CISA), takes into account suggestions made by the public over the initial ZTMM version.
Johnson Controls, the industry leader in smart, healthy and sustainable building technologies, today unveiled the details of its new OpenBlue Service: Ensuring Security Device Performance offering for 2023. This service is intended to assist clients in managing risk, enhancing building safety and optimising the return on their security technology investments. In addition to the ability to monitor and control security devices from many vendors, the offering includes the Johnson Controls OpenBlue suite of connected solutions, remote support services, insightful analysis from qualified engineers, and simpler, integrated zero-trust cybersecurity protection.