Regulatory Pressures
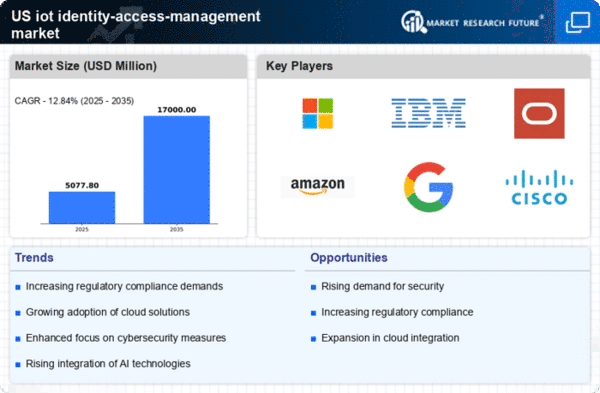
Regulatory frameworks in the US are becoming more stringent, compelling organizations to adopt comprehensive identity and access management solutions. Compliance with regulations such as the Health Insurance Portability and Accountability Act (HIPAA) and the General Data Protection Regulation (GDPR) necessitates robust identity management practices. The iot identity-access-management market is likely to benefit from this trend, as organizations invest in solutions that ensure compliance and protect sensitive information. In 2025, it is anticipated that the cost of non-compliance could reach billions of dollars, further incentivizing businesses to prioritize identity management. As regulatory pressures mount, the market for identity and access management solutions is expected to grow, driven by the need for compliance and risk mitigation.
Adoption of IoT Devices
The proliferation of IoT devices across various industries is significantly influencing the iot identity-access-management market. As more devices connect to networks, the need for effective identity management becomes critical to ensure secure access and data integrity. In 2025, the number of connected IoT devices is projected to exceed 30 billion in the US alone, creating a complex landscape for identity management. Organizations are increasingly recognizing that traditional security measures are inadequate for managing the vast number of devices. Consequently, the demand for advanced identity and access management solutions tailored for IoT environments is expected to rise, driving market expansion. This trend underscores the necessity for scalable and flexible identity management systems that can accommodate the growing number of connected devices.
Increased Cloud Adoption
The shift towards cloud-based services is reshaping the iot identity-access-management market. As organizations migrate their operations to the cloud, the demand for secure identity management solutions that can seamlessly integrate with cloud environments is on the rise. In 2025, it is projected that over 80% of enterprises will utilize cloud services, necessitating effective identity and access management strategies. This transition presents both challenges and opportunities for the market, as organizations seek to protect their data in increasingly complex environments. The need for solutions that provide visibility and control over user access in cloud applications is likely to drive innovation and growth in the iot identity-access-management market.
Rising Cybersecurity Threats
The increasing frequency and sophistication of cyberattacks is a primary driver for the iot identity-access-management market. Organizations are compelled to adopt robust identity and access management solutions to safeguard sensitive data and critical infrastructure. In 2025, it is estimated that cybercrime will cost businesses globally over $10 trillion annually, highlighting the urgency for enhanced security measures. The iot identity-access-management market is expected to grow as companies seek to mitigate risks associated with unauthorized access and data breaches. This trend is particularly pronounced in sectors such as finance and healthcare, where the stakes are exceptionally high. As organizations prioritize cybersecurity, investments in identity management solutions are likely to surge, further propelling market growth.
Growing Demand for User Experience
The emphasis on enhancing user experience is becoming a crucial driver in the iot identity-access-management market. Organizations are recognizing that seamless access to applications and services is vital for user satisfaction and productivity. As a result, there is a growing demand for identity management solutions that balance security with user convenience. In 2025, it is estimated that companies prioritizing user experience will see a 20% increase in customer retention rates. This trend is prompting vendors to develop solutions that streamline authentication processes while maintaining robust security measures. The focus on user experience is likely to shape the future of the iot identity-access-management market, as organizations strive to create secure yet user-friendly environments.