Rising Cyber Threats
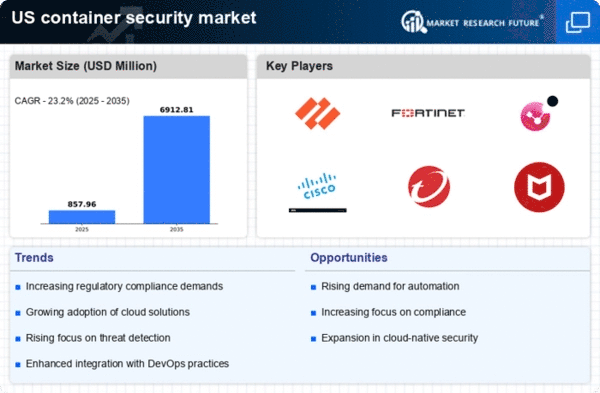
The container security market is experiencing heightened demand due to the increasing frequency and sophistication of cyber threats. Organizations are recognizing the vulnerabilities associated with containerized applications, which are often targeted by malicious actors. In 2025, it is estimated that cybercrime will cost businesses globally over $10 trillion annually, prompting a shift towards robust security measures. This trend is particularly pronounced in the US, where regulatory bodies are emphasizing the need for enhanced security protocols. As a result, companies are investing in container security solutions to safeguard their applications and data, thereby driving growth in the container security market.
Increased Cloud Adoption
the container security market is growing due to the accelerated adoption of cloud technologies. As businesses migrate to cloud environments, the need for effective security solutions becomes paramount. In 2025, it is anticipated that over 80% of enterprises will utilize cloud services, creating a fertile ground for container security solutions. The dynamic nature of cloud environments necessitates robust security measures to protect containerized applications from potential threats. Consequently, organizations are investing in container security technologies to ensure the integrity and confidentiality of their data, thereby propelling the container security market.
Regulatory Compliance Pressure
the container security market is driven by the need to comply with various regulatory frameworks. In the US, regulations such as the Health Insurance Portability and Accountability Act (HIPAA) and the General Data Protection Regulation (GDPR) necessitate stringent security measures for data protection. Organizations are increasingly adopting container security solutions to ensure compliance and avoid hefty fines, which can reach up to $20 million or 4% of annual global turnover. This compliance-driven approach is fostering a robust demand for container security technologies, as businesses seek to mitigate risks associated with non-compliance.
Shift Towards DevSecOps Practices
The container security market is benefiting from the growing adoption of DevSecOps practices, which integrate security into the software development lifecycle. This paradigm shift encourages organizations to prioritize security from the outset, rather than as an afterthought. In 2025, it is projected that 70% of organizations will implement DevSecOps, leading to increased investments in container security solutions. By embedding security measures within the development process, companies can reduce vulnerabilities and enhance the overall security posture of their applications. This trend is likely to propel the container security market forward as organizations seek to streamline their security efforts.
Demand for Scalability and Flexibility
The container security market is witnessing increased demand for solutions that offer scalability and flexibility. As organizations expand their digital infrastructure, the ability to scale security measures in tandem with growth becomes crucial. In 2025, it is expected that the container security market will grow at a CAGR of 25%, driven by the need for adaptable security solutions. Companies are seeking container security technologies that can seamlessly integrate with their existing systems while providing robust protection against evolving threats. This demand for scalable and flexible security solutions is likely to continue shaping the container security market.