Top Industry Leaders in the Security Software Telecom Market

Competitive Landscape of Security Software in Telecom Market:
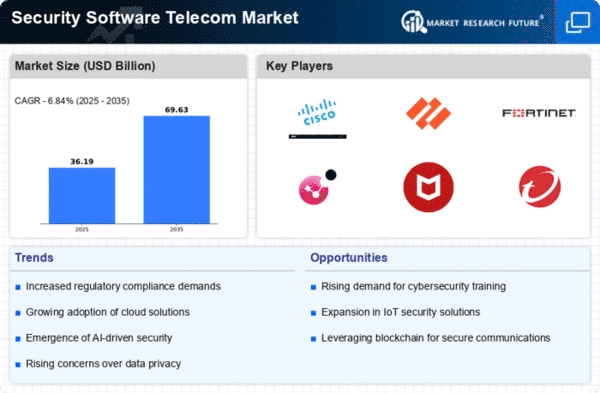
The telecom sector is undergoing a significant digital transformation, leading to increased vulnerability to cyberattacks. Consequently, the demand for robust security software solutions is soaring, propelling the growth of the security software market in the telecom space. This market is characterized by a dynamic and competitive landscape, with established players vying for dominance alongside emerging companies bringing innovative solutions to the table.
Key Players in the Security Software Market for Telecom:
- IBM Corporation (US)
- Dell Inc (US)
- Symantec Corporation (US)
- Trend Micro (Japan) Inc.
- McAfee (US)
- Check Point (US)
- CyberArk (Israel)
- Oracle Corporation (US)
- Imperva (US)
- F-Secure (Finland)
- Qualys (US),
- HP Enterprise Development LP (US)
- Forcepoint (US)
- FireEye (US)
- Fortinet (US)
- Microsoft Corporation (US)
- Amazon Web Services (US)
- Proofpoint (US), Palo Alto Networks (US)
- F5 Networks (US), Rapid7 (US)
- Juniper Networks (US)
- Sophos (UK)
The major players in this market include:
- Established giants: IBM, Symantec, McAfee, Dell EMC, Trend Micro, Imperva, AVG Technologies, Cisco Systems, Check Point Software Technologies, Fortinet, F-Secure, Websense, Sophos, Tripwire, Zscaler, Avast Software, Panda Security
- Promising newcomers: Darktrace, Exabeam, SentinelOne, CrowdStrike, Palo Alto Networks, Trellix
- Telecom-specific security solutions providers: DigiCert, Allot Communications, Enea AB, Spirent Communications
Strategies Adopted by Leading Players
The key players in the security software market for telecom are adopting various strategies to gain a competitive edge, including:
- Product portfolio expansion: Developing comprehensive security solutions that encompass a wide range of threats, including network security, cloud security, endpoint security, and application security.
- Innovation and technological advancements: Investing heavily in research and development to stay ahead of the evolving threat landscape and introduce innovative solutions like AI-powered security tools and blockchain-based security frameworks.
- Strategic partnerships and collaborations: Partnering with other technology companies, telecom operators, and security vendors to extend their reach and offer integrated solutions.
- Mergers and acquisitions: Engaging in mergers and acquisitions to expand their market share, acquire new technologies, and consolidate their position in the market.
- Subscription-based pricing models: Transitioning from traditional perpetual licensing models to subscription-based pricing models to cater to the evolving customer preferences and generate recurring revenue streams.
Factors for Market Share Analysis
Several key factors influence market share analysis in the competitive landscape of the security software market for telecom:
- Market size and growth rate: The size and growth rate of the overall telecom market, as well as the specific segments within the market, significantly impact the demand for security software solutions.
- Product portfolio and features: The breadth and depth of the product portfolio, along with the specific features and functionalities offered, are crucial factors influencing customer choice.
- Reputation and brand recognition: Established players with a strong reputation and brand recognition often enjoy an advantage in market share due to customer trust and loyalty.
- Pricing and licensing models: Competitive pricing strategies and flexible licensing models can attract cost-conscious customers and increase market penetration.
- Customer service and support: Responsive and efficient customer service and support play a vital role in customer satisfaction and retention.
- Compliance and certifications: Meeting industry standards and regulatory compliance requirements are critical for securing contracts with major telecom operators.
New and Emerging Companies
Several new and emerging companies are entering the security software market for telecom, bringing innovative solutions and disrupting the traditional landscape. These companies are focusing on specific niches within the market, leveraging cutting-edge technologies, and offering competitive pricing models. They are also actively engaging with telecom operators and participating in industry events to gain visibility and establish a presence in the market.
Current Company Investment Trends
Current investment trends in the security software market for telecom revolve around:
- Cloud-based security solutions: As more telecom operators migrate their infrastructure to the cloud, the demand for cloud-based security solutions is skyrocketing.
- AI-powered security tools: Artificial intelligence is transforming cybersecurity, and companies are investing heavily in developing AI-powered security solutions that can detect and prevent sophisticated cyberattacks.
- Security automation: Automation is playing an increasingly crucial role in streamlining security operations and reducing costs. Companies are investing in security automation solutions that can automate routine tasks, freeing up human resources for more strategic activities.
- Zero-trust security models: The zero-trust security model is gaining traction in the telecom industry, and companies are investing in solutions that adopt this approach to provide comprehensive security within the network.
- Integrated security platforms: Telecom operators require unified security platforms that offer a holistic view of their security posture and enable centralized management of security solutions. Companies are focusing on developing integrated platforms that consolidate their security offerings and cater to this demand.
Latest Company Updates:
Telecom operators will be able to offer premium 5G use cases that call for high throughput, dependability, and low latency in 2023 thanks to a new software toolkit that Swedish telecom equipment manufacturer Ericsson unveiled on Tuesday. Examples of these use cases include mobile cloud gaming, video conferencing, live broadcasting, remote-controlled machines and vehicles, public safety services, and potential Extended Reality (XR) applications.
Cisco, a US-based manufacturer of telecom equipment, introduced the Networking Cloud Platform in 2023 to make networking equipment management easier with a single, shared interface. The platform has been released in tandem with improvements to a number of Cisco products, such as the Catalyst portfolio and the ThousandEyes infrastructure monitoring service.