Rising Security Concerns
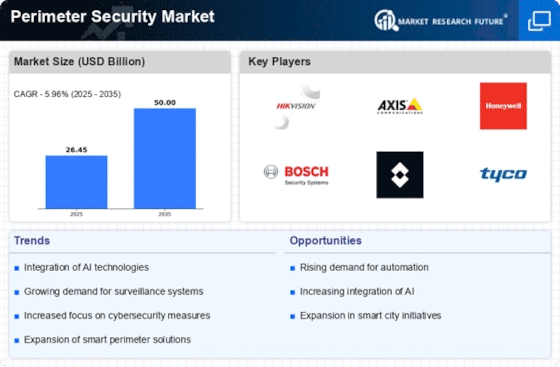
The increasing frequency of security breaches and threats has heightened the demand for robust perimeter security solutions. Organizations across various sectors are prioritizing the protection of their assets, leading to a surge in investments in perimeter security technologies. In 2025, the perimeter security market is projected to reach a valuation of approximately 30 billion USD, reflecting a compound annual growth rate of around 8%. This trend indicates that businesses are recognizing the necessity of safeguarding their premises against unauthorized access and potential threats. As a result, the perimeter security market is witnessing a shift towards more sophisticated solutions that can effectively mitigate risks and enhance overall security posture.
Technological Advancements
The perimeter security market is experiencing a transformative phase driven by rapid technological advancements. Innovations such as artificial intelligence, machine learning, and advanced surveillance systems are reshaping the landscape of security solutions. These technologies enable real-time monitoring, threat detection, and automated responses, significantly improving the effectiveness of perimeter security measures. In 2025, it is estimated that the integration of smart technologies will account for a substantial portion of the market, as organizations seek to leverage these advancements to enhance their security frameworks. Consequently, the perimeter security market is evolving to incorporate cutting-edge solutions that not only address current security challenges but also anticipate future threats.
Increased Regulatory Requirements
The perimeter security market is influenced by a growing emphasis on regulatory compliance and standards. Governments and regulatory bodies are implementing stringent guidelines to ensure the safety and security of critical infrastructure and sensitive information. Organizations are compelled to adopt perimeter security measures that align with these regulations, driving demand for compliant solutions. In 2025, it is projected that the market will see a notable increase in the adoption of security systems that meet regulatory requirements, as businesses strive to avoid penalties and enhance their reputations. This trend underscores the importance of integrating compliance into the perimeter security market, as organizations recognize that adherence to regulations is essential for maintaining operational integrity.
Growing Awareness of Security Risks
There is a notable increase in awareness regarding security risks among organizations and individuals, which is driving the perimeter security market. As incidents of theft, vandalism, and cyber threats become more prevalent, stakeholders are recognizing the importance of investing in effective perimeter security solutions. In 2025, it is expected that this heightened awareness will lead to a significant uptick in demand for advanced security technologies. Organizations are likely to allocate more resources towards enhancing their perimeter defenses, thereby contributing to the overall growth of the market. This trend suggests that the perimeter security market is evolving in response to changing perceptions of security, with a focus on proactive measures to mitigate risks.
Expansion of Infrastructure Projects
The ongoing expansion of infrastructure projects worldwide is significantly impacting the perimeter security market. As new facilities, transportation networks, and urban developments emerge, the need for effective security measures becomes paramount. In 2025, it is anticipated that investments in infrastructure will lead to a corresponding increase in demand for perimeter security solutions. This trend is particularly evident in sectors such as transportation, energy, and public safety, where securing perimeters is critical to safeguarding assets and ensuring public trust. Consequently, the perimeter security market is poised to benefit from the growth of infrastructure initiatives, as stakeholders prioritize the implementation of comprehensive security strategies.