Evolving Regulatory Landscape
The evolving regulatory landscape surrounding data protection and privacy is significantly influencing the ai in-cybersecurity market. As regulations become more stringent, organizations are compelled to adopt advanced cybersecurity measures to ensure compliance. The introduction of laws such as the California Consumer Privacy Act (CCPA) and the General Data Protection Regulation (GDPR) has heightened the focus on data security. Companies are increasingly turning to AI-driven solutions to automate compliance processes and enhance their ability to protect sensitive information. This trend is expected to drive growth in the ai in-cybersecurity market, as businesses seek to navigate complex regulatory requirements while safeguarding their data assets.
Rising Cyber Threat Landscape
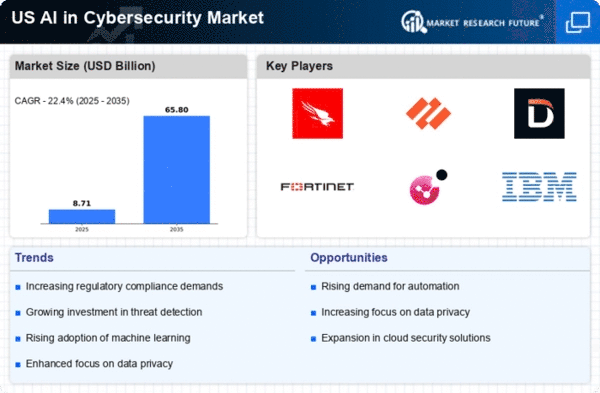
The escalating frequency and sophistication of cyber threats are driving the demand for advanced solutions in the AI in Cybersecurity market. Organizations are increasingly targeted by cybercriminals, with a reported 30% rise in ransomware attacks in the past year alone. This alarming trend compels businesses to adopt AI-driven cybersecurity measures that can proactively identify and mitigate risks. AI in Cybersecurity Market is projected to reach $38 billion by 2026, reflecting a compound annual growth rate (CAGR) of 23%. As threats evolve, the need for adaptive and intelligent security solutions becomes paramount, positioning AI as a critical component in safeguarding sensitive data and maintaining operational integrity.
Demand for Real-Time Threat Detection
The demand for real-time threat detection capabilities is a key driver in the ai in-cybersecurity market. Organizations are increasingly recognizing the necessity of immediate threat identification and response to mitigate potential damages. AI technologies enable continuous monitoring and analysis of network traffic, allowing for the swift detection of anomalies that may indicate a security breach. Reports suggest that companies employing AI for threat detection can identify breaches up to 60% faster than those relying solely on traditional methods. This capability not only enhances security but also instills greater confidence among stakeholders, further propelling the adoption of AI solutions in the cybersecurity landscape.
Growing Investment in Cybersecurity Solutions
Investment in cybersecurity solutions is witnessing a significant uptick, driven by the increasing recognition of cyber risks. The ai in-cybersecurity market is benefiting from this trend, as organizations allocate more resources to protect their digital assets. In 2025, it is estimated that U.S. businesses will spend over $150 billion on cybersecurity, with a substantial portion directed towards AI-driven technologies. This influx of capital is fostering innovation and the development of cutting-edge solutions that can address emerging threats. As organizations prioritize cybersecurity, the ai in-cybersecurity market is poised for robust growth, with new entrants and established players alike striving to capture market share.
Integration of AI with Existing Security Frameworks
The integration of AI technologies with existing cybersecurity frameworks is becoming increasingly prevalent, as organizations seek to enhance their security posture. This trend is particularly evident in the ai in-cybersecurity market, where companies are leveraging AI to augment traditional security measures. By incorporating machine learning algorithms and automated threat detection systems, businesses can improve their response times and reduce the likelihood of breaches. In fact, studies indicate that organizations utilizing AI-driven solutions experience a 50% reduction in incident response times. This integration not only streamlines security operations but also allows for more efficient resource allocation, ultimately leading to cost savings and improved security outcomes.
.png)