Top Industry Leaders in the Threat Intelligence Management Market

Competitive Landscape of Threat Intelligence Management Market: Navigating a Dynamic Terrain
The ever-evolving cyber threat landscape casts a long shadow over organizations worldwide. This constant state of vigilance makes robust threat intelligence management solutions not just desirable, but indispensable. Understanding the competitive landscape of this burgeoning market becomes critical for both established players and potential entrants.
Key Players:
-
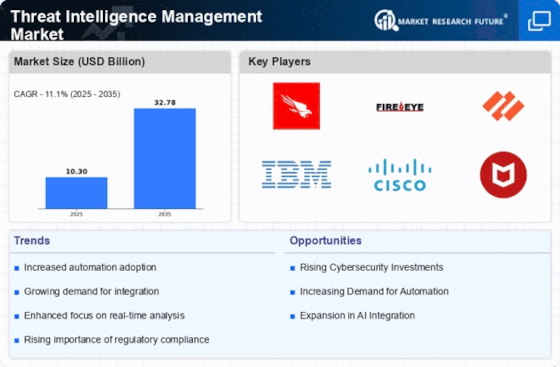
IBM Corporation
-
Cisco System Inc.
-
Microsoft
-
BlackBerry Limited
-
Check Point Software Technologies
-
Huawei Technologies
-
Anomali Inc
-
AO Kaspersky Lab
-
CrowdStrike Inc.
-
Fortinet Inc.
-
Vmware Inc
Strategies for Growth and Differentiation:
Competition in the TIM market is fierce, prompting players to adopt various strategies to stand out:
-
Specialization: Some vendors focus on specific industry verticals or threat actor groups, offering tailored intelligence reports and threat feeds.
-
Integration: Many players are integrating TIM functionalities with broader security platforms, simplifying threat analysis and response workflows.
-
AI and Machine Learning: Leveraging AI and ML for data analysis and detection of sophisticated threats is becoming a key differentiator.
-
Partnerships and Open Source Intelligence: Collaborations with other security vendors and leveraging open-source intelligence communities are gaining traction.
-
Cloud-based Solutions: The shift towards cloud-based TIM solutions is gaining momentum due to their scalability and cost-effectiveness.
Factors for Market Share Analysis:
Understanding market share distribution in the TIM landscape is crucial for assessing a player's competitive position. Key factors to consider include:
-
Revenue generated from TIM solutions.
-
Number of deployed customers and their size and industry profiles.
-
Geographical reach and market penetration in different regions.
-
Breadth and depth of threat intelligence coverage.
-
Customer satisfaction and brand reputation.
Emerging Players and Disruptive Technologies:
The TIM market is constantly evolving, with new and innovative players entering the scene. Some up-and-coming companies to watch include:
-
Cybersixgill: They utilize dark web and open-source intelligence to provide early warnings of potential attacks targeting specific organizations.
-
ThreatQuotient: Their platform allows for orchestration and collaboration between disparate security tools, streamlining the threat intelligence workflow.
-
XForce: IBM's security division offers XForce Threat Intelligence, a comprehensive source of global threat data and analysis.
Investment Trends and Future Outlook:
Current trends in TIM investment reveal a focus on areas like:
-
Advanced analytics and automation: Automating threat detection and response processes using AI and ML.
-
Predictive capabilities: Utilizing threat intelligence to anticipate future attacks and proactively strengthen defenses.
-
Integration with existing security infrastructure: Ensuring seamless integration of TIM solutions with existing security tools and platforms.
-
Global expansion: Targeting high-growth markets and tailoring solutions to regional threat landscapes.
The future of the TIM market is brimming with potential. The increasing sophistication of cyber threats, coupled with growing regulatory demands and organizational awareness, will continue to fuel its growth. Players who adapt to these trends, embrace innovation, and deliver tangible value to customers will be best positioned to capitalize on this dynamic and lucrative market.
Latest Company Updates:
-
October 26, 2023: Palo Alto Networks announced the acquisition of CloudStrike, a leading threat intelligence provider. This move is expected to strengthen Palo Alto's threat intelligence capabilities.
-
November 15, 2023: Mandiant, a cybersecurity firm, launched a new threat intelligence platform called "Mandiant Advantage." The platform combines Mandiant's expertise with threat intelligence from various sources.
-
December 5, 2023: The Cybersecurity and Infrastructure Security Agency (CISA) released a report on "Cybersecurity Challenges in 2024." The report highlights the importance of threat intelligence in mitigating cyber threats.