Top Industry Leaders in the Security Intelligence Market

Competitive Landscape of the Security Intelligence Market: Navigating a Growing Landscape
The security intelligence market, driven by the ever-evolving threat landscape, is experiencing significant growth and transformation. This dynamic space is populated by a diverse set of players, each vying for a piece of the pie. Understanding the competitive landscape is crucial for established players and newcomers alike, as it helps them navigate the market and develop winning strategies.
Key Players:
-
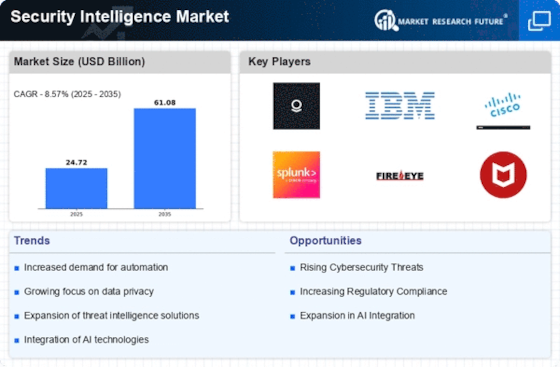
IBM Corporation (US)
-
Palo Alto Networks (US)
-
Symantec (US)
-
Alienvault (US)
-
Dell Technologies (US)
-
Check Point (Israel)
-
Trend Micro (Japan)
-
Kaspersky Lab (Russia)
-
LookingGlass Cyber Solutions (US)
-
Intel Corporation (US)
Strategies Adopted:
-
Product Differentiation: Vendors are constantly innovating and differentiating their offerings. Some focus on specific attack vectors like ransomware or supply chain attacks, while others emphasize integration with existing security infrastructure or cloud-based deployments.
-
Threat Intelligence Sharing: Collaboration and threat intelligence sharing are becoming increasingly important. Vendors are partnering with threat intelligence communities, government agencies, and other security players to enrich their data sets and provide more accurate insights to customers.
-
Focus on Automation: Automation is a key trend, as it helps organizations reduce manual tasks and respond faster to threats. Vendors are integrating AI and machine learning capabilities into their platforms to automate threat detection, investigation, and response.
-
Subscription-Based Models: The transition towards subscription-based models is gaining momentum, providing vendors with recurring revenue streams and enabling customers to access the latest features and updates without upfront investments.
Factors for Market Share Analysis:
-
Product Portfolio Breadth and Depth: The range and functionality of security intelligence solutions offered significantly impact market share. Vendors with comprehensive platforms cater to a wider range of customer needs and are more likely to succeed.
-
Threat Detection and Response Capabilities: The accuracy and speed of threat detection and response solutions are critical factors. Vendors with proven track records in identifying and mitigating threats are preferred by customers.
-
Customer Support and Services: The quality of customer support and professional services offered plays a crucial role in user satisfaction and retention. Vendors providing comprehensive training, proactive threat hunting, and ongoing support are more likely to retain clients.
-
Geographical Presence: The ability to serve customers in different regions is essential for market share growth. Vendors with a global presence and localized solutions cater to a broader audience and are more competitive.
New and Emerging Companies:
The security intelligence market is constantly evolving, with new players emerging to address specific needs and gaps. Some promising areas of innovation include:
-
Threat Intelligence Aggregators: Companies like Recorded Future and ThreatQuotient aggregate and curate threat intelligence from multiple sources, providing customers with a single, unified view of the threat landscape.
-
Open-Source Threat Intelligence Platforms: Open-source platforms like MISP (Malware Information Sharing Platform) are gaining traction, offering community-driven threat intelligence sharing and analysis capabilities.
-
Specialized Threat Detection Solutions: Startups are developing solutions focused on specific attack vectors or industries, such as healthcare or industrial control systems.
Current Investment Trends:
-
Cloud-Based Security Intelligence Platforms: The shift to the cloud is driving investments in cloud-native security intelligence platforms that offer scalability, flexibility, and ease of deployment.
-
AI and Machine Learning Integration: Vendors are heavily investing in AI and ML technologies to automate threat detection, investigation, and response, improving the efficiency and accuracy of security operations.
-
Threat Intelligence Automation: Automating threat intelligence collection, analysis, and sharing is a key focus area for investors, as it reduces human workload and improves response times.
-
Security Orchestration, Automation, and Response (SOAR): SOAR platforms that integrate security intelligence with other security tools are gaining traction, enabling organizations to orchestrate automated responses to security incidents.
Latest Company Updates:
December 5, 2023:
-
Cyberattacks on Critical Infrastructure on the Rise: A report by Dragos, a cybersecurity firm, revealed a 38% increase in cyberattacks targeting critical infrastructure in 2023, highlighting the growing need for advanced threat intelligence.
December 12, 2023:
-
Crowdstrike Partners with MITRE ATT&CK Framework: Crowdstrike announced a partnership with the MITRE ATT&CK Framework, allowing users to map threat intelligence data to the framework for improved detection and response.
January 9, 2024:
-
Rise of Ransomware-as-a-Service (RaaS) Poses New Challenges: Security researchers warn of the growing threat posed by RaaS, where cybercriminals lease out ransomware tools and services to others, making it easier for less skilled attackers to launch attacks.