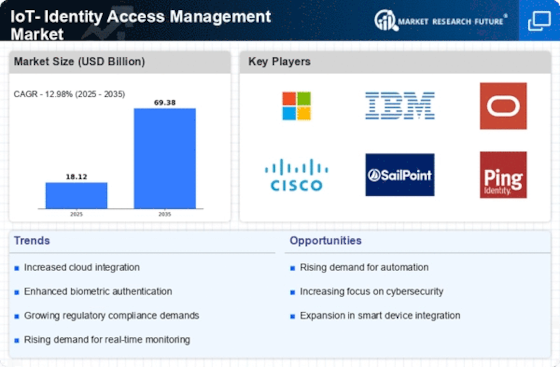
Top Industry Leaders in the IOT Identity Access Management Market

Competitive Landscape of IOT- Identity Access Management Market:
The Internet of Things (IoT) Identity Access Management (IAM) market, where tiny devices dance to the tune of secure identity. From ensuring smart refrigerators don't order too much milk to safeguarding industrial robots from cyberattacks, IoT IAM empowers a connected world with robust security and controlled access. In this dynamic arena, established giants and nimble innovators clash, all vying for a bigger slice of the digital ID pie. Let's dissect the key strategies and players shaping this captivating scene.
Key Players:
- Hitachi, Ltd.
- EMC Corporation
- ARCON Tech Solutions
- Cloud Security Alliance
- CA Technologies
- IBM Corporation
- Microsoft Corporation
- Intel Security Group
- Siemens AG
- Oracle Corporation
Strategies Adopted by key Players:
- Technological Differentiation: Companies compete fiercely on technological advancements, focusing on factors like enhanced device authentication protocols, multi-factor authentication for robust security, secure device provisioning and lifecycle management, and seamless integration with diverse IoT platforms. Developing advanced data encryption technologies, optimizing identity management platforms for scalability, and integrating AI-powered anomaly detection for proactive threat prevention are key differentiators.
- Expanding Application Reach: Moving beyond traditional consumer IoT devices to address the needs of diverse sectors like industrial automation, smart cities, healthcare, and critical infrastructure unlocks new market segments and drives wider adoption. Developing specialized IoT IAM solutions for specific industries and use cases is crucial.
- Addressing Cost and Ease of Use: Making IoT IAM solutions more affordable and user-friendly is vital for widespread adoption. Offering flexible pricing models, simplifying user interfaces for managing device identities, and reducing deployment and maintenance costs are key strategies.
- Building Partnerships and Collaborations: Fostering partnerships with IoT platform providers, hardware manufacturers, cybersecurity firms, and system integrators accelerates innovation, shares expertise, and expands market reach. Collaborating on industry standards, developing reference architectures, and promoting the benefits of secure IoT access contribute to market growth.
Factors for Market Share Analysis:
- Revenue Generated: This straightforward metric reflects a company's market penetration and financial strength.
- Number of Deployed Solutions: Understanding the volume of deployed IoT IAM systems provides insight into customer adoption and market reach.
- Technology Advancements: Assessing a company's investment in R&D, patent portfolio, and cutting-edge IoT IAM technologies helps gauge its future competitive edge.
- Customer Satisfaction: Analyzing user feedback and loyalty metrics reveals how effectively a company caters to customer needs and builds brand reputation.
Latest Company Updates:
October 2023- SailPoint Technologies, Inc.'s subsidiary in the United Kingdom finished the purchase of Osirium, a UK security company focused on addressing complex access needs. This acquisition will probably combine visibility, control, and safeguarding across all access kinds, including highly sensitive and regular, into a single solution.
September 2023- Venafi, a cybersecurity solutions company and pioneer of machine identity management, unveiled Venafi Athena at its 5th annual Machine Identity Management Summit. The solution harnesses the capabilities of machine learning, large language models, and Venafi's industry-leading data assets to simplify and accelerate machine identity management for security and platform teams.