Increasing Cyber Threat Landscape
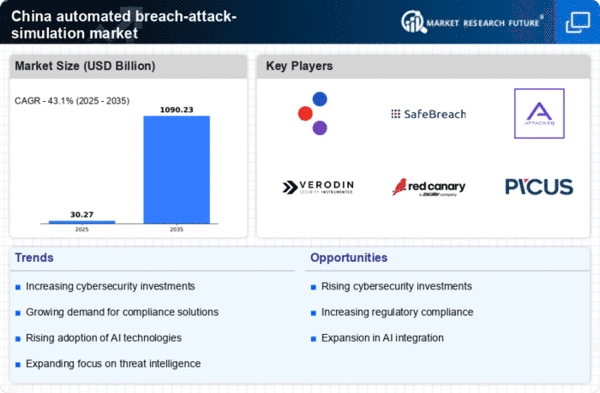
The escalating cyber threat landscape in China is a primary driver for the automated breach-attack-simulation market. As organizations face a growing number of sophisticated cyberattacks, the need for proactive security measures becomes paramount. In 2025, it is estimated that cybercrime could cost the Chinese economy over $1 trillion, highlighting the urgency for businesses to adopt advanced security solutions. Automated breach-attack simulations allow organizations to identify vulnerabilities and assess their security posture effectively. This proactive approach not only helps in mitigating risks but also enhances the overall resilience of organizations against potential breaches. Consequently, the increasing frequency and complexity of cyber threats are likely to propel the demand for automated breach-attack-simulation solutions across various sectors in China.
Government Initiatives and Support
The Chinese government has been actively promoting cybersecurity initiatives, which significantly impacts the automated breach-attack-simulation market. With the implementation of the Cybersecurity Law and various national strategies aimed at enhancing cybersecurity infrastructure, organizations are encouraged to adopt advanced security measures. In 2025, government funding for cybersecurity initiatives is projected to reach approximately $10 billion, fostering innovation and development in the sector. This support not only drives awareness but also incentivizes businesses to invest in automated breach-attack-simulation technologies. As a result, the alignment of government policies with market needs is likely to create a conducive environment for the growth of the automated breach-attack-simulation market in China.
Rising Demand for Compliance Solutions
The increasing emphasis on compliance with cybersecurity regulations is a significant driver for the automated breach-attack-simulation market. Organizations in China are required to adhere to various regulations, such as the Personal Information Protection Law (PIPL) and the Data Security Law. These regulations necessitate robust security measures to protect sensitive data. In 2025, it is estimated that compliance-related expenditures in the cybersecurity sector will account for over 30% of total cybersecurity budgets. Automated breach-attack simulations provide organizations with the tools to test their compliance readiness and identify gaps in their security frameworks. This growing demand for compliance solutions is likely to fuel the adoption of automated breach-attack-simulation technologies across multiple industries in China.
Growing Awareness of Cybersecurity Training
The growing awareness of the importance of cybersecurity training is influencing the automated breach-attack-simulation market. Organizations in China are recognizing that human error is a significant factor in security breaches, prompting a shift towards comprehensive training programs. In 2025, it is estimated that investments in cybersecurity training will exceed $5 billion, underscoring the commitment to enhancing employee awareness and skills. Automated breach-attack simulations serve as effective training tools, allowing employees to experience realistic attack scenarios and learn how to respond effectively. This focus on training and preparedness is likely to drive the adoption of automated breach-attack-simulation solutions, as organizations aim to cultivate a security-conscious culture.
Technological Advancements in Cybersecurity
Technological advancements in cybersecurity are driving innovation within the automated breach-attack-simulation market. The integration of cutting-edge technologies, such as artificial intelligence and machine learning, enhances the effectiveness of breach simulations. In 2025, the market for AI-driven cybersecurity solutions in China is projected to grow by 25%, indicating a strong trend towards automation and intelligence in security practices. These advancements enable organizations to conduct more realistic simulations, providing deeper insights into potential vulnerabilities. As businesses seek to stay ahead of cyber threats, the demand for sophisticated automated breach-attack-simulation tools is likely to increase, reflecting the broader trend of technological evolution in the cybersecurity landscape.