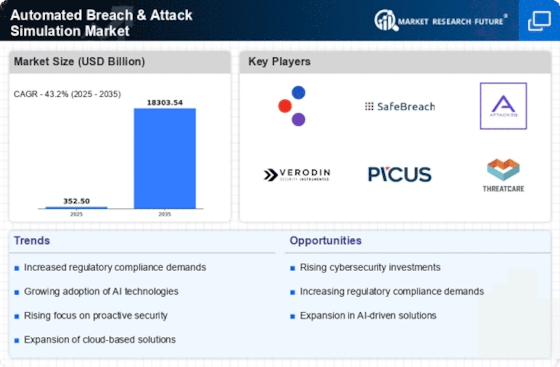
Top Industry Leaders in the Automated Breach Attack Simulation Market

Competitive Landscape of the Automated Breach & Attack Simulation (BAS) Market:
The Automated Breach & Attack Simulation market is experiencing explosive growth, fueled by the ever-escalating cyber threat landscape. Organizations are scrambling to bolster their defenses, and BAS solutions – which mimic real-world attacker tactics to uncover vulnerabilities – are becoming essential tools. Understanding the competitive landscape is crucial for both vendors and potential customers navigating this dynamic market.
Key Players:
-
XM Cyber (Israel)
-
Cymulate (Israel)
-
Aujas (US)
-
Elasticito Limited (UK)
-
SafeBreach Inc. (US)
-
Optiv Security Inc. (US)
-
Traxion (Netherlands)
-
Layer 8 Solutions (Canada)
-
Carbonsec (Slovenia)
-
Marlabs Inc. (US)
-
Netsecuris LLC (US)
-
Guardicore (Israel)
-
Larsen & Toubro Infotech Limited (India)
-
eSafe IT (Ethiopia)
Strategies and Differentiation:
-
Attack Tactic Sophistication: Players compete on the realism and comprehensiveness of their attack simulations, encompassing the latest zero-day vulnerabilities, evolving attacker techniques, and industry-specific attack scenarios.
-
Integration and Automation: Integrating BAS with existing security tools and automating remediation workflows streamline incident response and improve overall security posture.
-
Continuous Improvement and Threat Intelligence: Regularly updating attack libraries with the latest threat intel and offering real-time attack insights keep organizations ahead of emerging threats.
-
Scalability and Customization: Delivering solutions that cater to diverse organizational sizes and compliance requirements, with flexible deployment options (on-premise, cloud, hybrid) and customizable attack simulations.
Market Share Analysis:
-
Revenue Share: Established security giants currently hold the largest revenue share due to their extensive customer base and bundled BAS offerings. However, pure-play BAS vendors are gaining traction with their specialized technology and competitive pricing.
-
Customer Acquisition and Focus: Large enterprises represent a significant revenue share, but vendors are increasingly targeting mid-sized companies and specific industry verticals with tailored solutions.
-
Geographic Breakdown: North America currently dominates the market, followed by Europe and Asia Pacific. Emerging markets present significant growth potential as cyber awareness and regulations gain traction.
New and Emerging Companies:
-
Attack Surface Management Vendors: Companies like Vectra AI and Kenna Security are integrating BAS capabilities into their attack surface management platforms, offering a holistic view of exposed vulnerabilities.
-
AI-Powered Solutions: Startups like Cybereason and Deepwatch are using AI and machine learning to automate attack simulations, threat detection, and incident response, improving efficiency and agility.
-
Open-Source BAS Tools: Projects like TheHive and Metasploit offer free and open-source BAS tools, expanding accessibility and fostering community-driven innovation, though they often lack enterprise-grade features and support.
Current Investment Trends:
-
Venture Capital Activity: BAS startups are attracting significant VC funding, reflecting the market's high growth potential. Investors are keen on AI-powered solutions, cloud-based offerings, and niche solutions for specific industries.
-
Acquisitions and Partnerships: Consolidation trends are emerging, with larger players acquiring smaller companies for their technological expertise or customer base. Strategic partnerships between BAS vendors and security ecosystem players are also fostering wider adoption and integration.
-
Focus on Innovation: Vendors are continuously investing in research and development, exploring advanced attack simulation techniques, integration with emerging technologies like blockchain, and expanding capabilities beyond vulnerability detection to include attack path analysis and incident response automation.
Latest Company Updates:
-
Dec 2023: Cymulate, a leading BAS provider, announced a partnership with Palo Alto Networks to integrate Cymulate's breach and attack simulation platform with Palo Alto Networks' Cortex XDR platform. This will offer organizations a more comprehensive security posture by combining attack simulation with endpoint detection and response.
-
Nov 2023: The Cybersecurity and Infrastructure Security Agency (CISA) released a report highlighting the importance of BAS in improving organizational cybersecurity posture. The report emphasizes the need for organizations to regularly test their defenses against real-world attacks using BAS solutions.
-
Oct 2023: AttackIQ, another major BAS player, acquired Coherra, a cloud-based security validation platform company. This acquisition strengthens AttackIQ's ability to offer comprehensive security validation solutions to organizations.