Top Industry Leaders in the Ransomware Protection Market
Competitive Landscape of the Ransomware Protection Market
The omnipresent threat of ransomware has ignited a burgeoning market for comprehensive protection solutions. This dynamic battlefield is teeming with established players, nimble startups, and a diverse range of strategies – all vying for a slice of the pie. With ransomware attacks evolving at breakneck speed, understanding the competitive landscape is crucial for both vendors and potential customers.
Key Players:
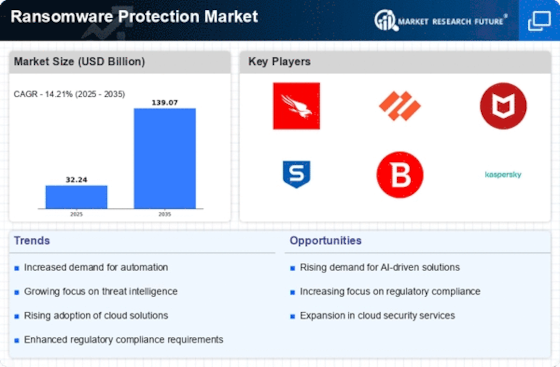
- Microsoft Corporation (U.S.)
- Sophos Ltd. (U.K)
- Intel Security (McAfee) (U.S.)
- Symantec Corporation (U.S.)
- Kaspersky Lab (Russia)
- Malware bytes Corp (U.S.)
- McAfee Inc. (U.S.)
- Avast Software S.R.O (Czech Republic)
- Cisco System Inc.(U.S.
- Palo Alto Networks Inc.(U.S.)
- Sentinelone (U.S.)
- Zscaler, Inc. (U.S.).
Strategies for Survival and Domination:
- AI and Machine Learning Integration: Integrating AI and machine learning (ML) algorithms is critical for early ransomware detection and automated incident response. Companies are investing heavily in ML-powered threat intelligence, anomaly detection, and behavioral analysis to stay ahead of attackers.
- Endpoint Protection Renaissance: The endpoint has become the epicenter of ransomware attacks. Vendors are bolstering endpoint security with advanced features like endpoint detection and response (EDR), application isolation, and vulnerability management.
- Zero-Trust Architecture: Implementing zero-trust security models with least-privilege access controls and segmentation can limit the spread of ransomware within an organization. Vendors are integrating zero-trust principles into their offerings to provide comprehensive protection beyond the perimeter.
- Collaboration and Partnerships: No single vendor can offer complete protection. Strategic partnerships with threat intelligence providers, managed security service providers (MSSPs), and incident response specialists are crucial for a holistic approach to ransomware defense.
Factors Dictating Market Share:
- Product Efficacy and Feature Depth: Solutions that consistently demonstrate robust detection, prevention, and recovery capabilities will win customer trust and market share.
- Deployment Flexibility and Scalability: Vendors offering cloud-based, SaaS, and on-premise deployment options cater to diverse customer needs and preferences.
- Pricing and Licensing Models: Competitive pricing and flexible licensing models, like subscription options, are crucial for attracting budget-conscious customers, particularly small and medium-sized businesses (SMBs).
- Customer Support and Training: Comprehensive customer support, extensive training resources, and proactive threat advisory services are essential for customer retention and satisfaction.
New Entrants and Disruptive Forces:
- Open-Source Solutions: Open-source ransomware protection tools like OSSEC and Wazuh are gaining traction, particularly within budget-constrained or security-conscious organizations. While offering cost-effectiveness and customization, open-source solutions require significant technical expertise for deployment and maintenance.
- Cybersecurity Insurance Providers: Insurance companies are increasingly offering bundled cybersecurity solutions, including ransomware protection, as part of their insurance packages. This trend may disrupt the traditional market landscape and influence customer buying decisions.
- Cloud-Based Security Orchestration, Automation, and Response (SOAR) Platforms: SOAR platforms can automate incident response workflows and streamline cybersecurity operations, potentially streamlining and simplifying ransomware defense.
Investment Trends and the Road Ahead:
- Focus on Automation and Orchestration: Vendors are heavily investing in AI-powered automation, orchestration, and incident response tools to increase efficiency and reduce human error in tackling ransomware attacks.
- Integration with Existing Security Stacks: Seamless integration with existing security infrastructure and platforms is crucial for customer adoption. Open APIs and interoperability are becoming key priorities for vendors.
- Expansion into Managed Security Services: Offering managed ransomware protection services as part of a broader security package is becoming increasingly attractive to resource-constrained organizations.
- Exploring Blockchain and Distributed Ledger Technology (DLT): The potential of blockchain to provide secure and tamper-proof data storage and access control is attracting interest in the ransomware protection space, although practical applications are still in their early stages.
Latest Company Updates:
Jan 12, 2024: Deepwatch, a leader in EDR and advanced threat detection, announced the acquisition of Vectra Networks, a prominent vendor in network traffic analysis and NDR. This strategic move combines their expertise to create a unified platform for comprehensive ransomware protection across endpoints and networks.
Jan 10, 2024: Crowdstrike, a cybersecurity giant, announced a collaboration with the MITRE ATT&CK framework to integrate its threat intelligence and adversary tactics into their Falcon platform. This partnership aims to enhance detection and response capabilities against real-world ransomware attacks.
Jan 8, 2024: Avast, a major antivirus provider, released a free decryption tool specifically targeting the Conti ransomware variant. This move demonstrates the industry's commitment to providing free resources and proactive countermeasures against prevalent ransomware threats.
Jan 5, 2024: The European Union proposed new cybersecurity legislation, the NIS 2 directive, which mandates companies to report ransomware attacks to authorities within 72 hours. This initiative aims to improve incident response coordination and transparency across the region.
Jan 3, 2024: Lloyds of London, a leading insurance provider, announced stricter underwriting requirements for cyber insurance policies, including mandatory multi-factor authentication and endpoint protection measures. This move reflects the growing concerns about cyber risks and the need for proactive security practices.